Big Data Management Exercises
Principle in Data Science Exercises
Data Analytics Exercises
Data Mining Exercises
Network Security Exercises
Other Exercises:
Python String Exercises
Python List Exercises
Python Library Exercises
Python Sets Exercises
Python Array Exercises
Python Condition Statement Exercises
Python Lambda Exercises
Python Function Exercises
Python File Input Output Exercises
Python Tkinter Exercises
Network Security - Exercises Section 2
21. What properties must a hash function have to be useful for message authentication?Ans:
1. H can be applied to a block of data of any size.
2. H produces a fixed-length output.
3. H(x) is relatively easy to compute for any given x, making both hardware and software implementations practical.
4. For any given value h, it is computationally infeasible to find x such that H(x) = h. This is sometimes referred to in the literature as the one-way property.
5. For any given block x, it is computationally infeasible to find y ≠ x with H(y) = H(x).
6. It is computationally infeasible to find any pair (x, y) such that H(x) = H(y).
22. In what way is the Diffie-Helman key exchange algorithm insecure against a man in-the-middle attack?
Ans:
Suppose Alice and Bob wish to exchange keys, and Darth is the adversary. The attack proceeds as follows:
1. Darth prepares for the attack by generating two random private keys XD1 and XD2, and then computing the corresponding public keys YD1 and YD2.
2. Alice transmits YA to Bob.
3. Darth intercepts YA and transmits YD1 to Bob. Darth also calculates
K2 = (YA)XD2 mod q.
4. Bob receives YD1 and calculates K1 = (YD1)XB mod q.
5. Bob transmits YB to Alice.
6. Darth intercepts YB and transmits YD2 to Alice. Darth calculates
K1 = (YB)XD1 mod q.
7. Alice receives YD2 and calculates K2 = (YD2)XA mod q.
At this point, Bob and Alice think that they share a secret key. Instead Bob and Darth share secret key K1, and Alice and Darth share secret key K2.
23. Perform encryption and decryption using the RSA algorithm for the following:
a) p=19; q=23; M = 2;
Ans:
n = pq = 437, @(n) = (p – 1)(q – 1) = 396
Find d and e so that de mod 396 = 1, find this number so that gcd of this number is d*e.
e = 29, de mod 396 = 1, so d = 41.
PU = {29, 437}, PR = {41, 437}
C = 229 mod 437
= [(2^10 mod 437)*(2^10 mod 437)*(2^9 mod 437)] mod 437
= [150*150*75] mod 437
= 243
b) p=7; q=31; M = 3;
Ans:
n = pq = 217, @(n) = (p – 1)(q – 1) = 180
Find d and e so that de mod 180 = 1, find this number so that gcd of this number is d*e.
e = 17, de mod 180 = 1, so d = 53.
PU = {17, 217}, PR = {53, 217}
C = 217 mod 217
= [(2^10 mod 217)*(2^7 mod 217)] mod 217
= [156*128] mod 437
= 4
24a. How does the P-Boxes improved security in the block encryption algorithm?
Ans:
The order of bits are rearranged after the P-boxes implementation. The redundancy of the plaintext to confuse the statistical structure of plaintext hence it can help to block attempts to reduce the key. The implementation of P-boxes also can help in hiding the relationship between ciphertext and plaintext.
24b. What will happen if a block encryption algorithm were to use only S-Boxes and no P-Boxes?
Ans:
For the case of initial and final Permutation. I think the security level will drop after removing P-Boxes. Without the P-Boxes it might be easier for hacker or attacker to break the code because the code only implement confusion but without diffusion technique. The relationship between the symmetric key and ciphertext will become complex after implements S-Boxes but without increasing the redundancy of the plaintext (because no P-Boxes) hence easier for attacker to break the code.
For the case of expansion P-Box, if no expansion P box is carried out then the S-Box also cannot carry out. This is because the bit number of input does not which is 32 bits cannot insert into S-boxes which requires 48 bits. The encryption process is terminated half way.
24c. State the attack scenario (e.g. ciphertext-only, known-plaintext, chosen-plaintext, chosen-ciphertext) in each of the following items.
i) Eve is able to intercept encrypted communication between Alice and Bob.
Ans:
Ciphertext only attack
ii) Eve is able to obtain the encryption of any plaintext that she wants.
Ans:
Chosen Plaintext attack
24d. S-boxes is one of the process in the Data Encryption Standard (DES) protocol.
i) Describe the function of S-boxes that makes DES a secure system.
Ans:
The DES employs 8 S-boxes each with a 6 bit input and 4 bit output, hence the total of 48 bits input after S-boxes will become 32 bit output. The S- boxes follow confusion technique. The implementation of confusion technique can help in obscuring the relaitonship between ciphertext and plaintext, in addition it can help in hiding the relaitonship between ciphertext and key in order to enhance the security of DES.
Referring to S-box[1] in Figure below, show that S1(x1) ⊕ S1(x2) ≠ S1(x1 ⊕ x2) for x1 = 000000 and x2 = 000001
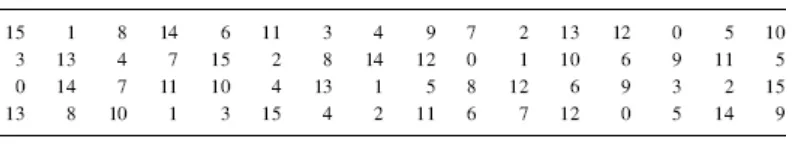
Ans:
x1 = 000000
we get 00 in binary which is 0 in decimal, row =0
we get 0000 in binary which is 0 in decimal, column =0
decimal 15 convert to binary 1111
x2 = 000001
we get 01 in binary which is 1 in decimal, row =1
we get 0000 in binary which is 0 in decimal, column =0
decimal 3 convert to binary 0011
S1(x1) ⊕ S1(x2) = S1(000000) ⊕ S1(000001)
= 1111 ⊕ 0011
= 1100
S1(x1 ⊕ x2) = S1(000001)
= 0011
Hence S1(x1) ⊕ S1(x2) ≠ S1(x1 ⊕ x2) where 1100 ≠ 0011
e) Consider a security system that uses Cipher Block Chaining (CBC) mode to increase its encryption safety.
i) Design and explain the CBC mode using an Advanced Encryption Standard (AES).
Ans:
For the case of encryption, the plaintext block (first block) initially xor with the initial vector (IV). Next, the result is encrypted to the ciphertext block. The encryption result from the first block will be XOR with plaintext text block until the last block. The existence of IV can help to generate different ciphertext block even with the same plaintext block input.
ii) What is the function of Initialization Vector (IV) in the CBC Mode and what happened if we remove the IV from the CBC.
Ans:
The Initialization Vector (IV) is to ensure same plaintext can be encrypted to form different ciphertexts. No harm is done if an adversary learns the IV after the plaintext has been encrypted, because it has serve its purpose. The IV can be made public since security of the system does not be impacted after encryption. In addition, it can prevent the decrption of the first ciphertext block is vulnerable to the introduction of bit errors in specific bit positions of the IV.
Without IV from the CBC, the same plaintext can be encrypted to form same ciphertexts. In addition, without the IV from the CBC, it is vulnerable to dictionary attack.
25. Let the input size of a block cipher be 16 bits and the block cipher is used in the electronic code book (ECB) mode of operation. Suppose we have the following plaintext where all blocks are encrypted using the same key:
(02 34 67 88 02 34 44 AB 67 88 B0 3F)hex
i) Give an example of a ciphertext if the above plaintext is encrypted using the said block cipher.
Ans:
ECB block cipher is 16 bits.
ii) Let say the encrypted important file is stored in this scheme and each data record has a size of 16 bits. The records are not related to one another. Is ECB mode still appropriate in this scenario? Please state your reason.
Ans:
Yes. The ECB mode is still appropriate in this scenario. This is because the plaintext or ciphertext block is encrypted or decrypted independently.
26a. Perform calculation of the given problems using the RSA algorithm.
i) You intercept the ciphertext C =10 sent to a user whose public key is e=5, n=35. What is the plaintext M?
Ans:
C = Me mod N 10 = M5 mod 35 M = 5
ii) The public key of a given user is e = 7, N = 33. What is the private key of this user?
Ans:
N= 33, So let’s assume p = 11 and q = 3
Ø(N) = (p-1) x (q-1) = 20
Calculate private key:
d x e = 1 mod 20
d x 7 = 1 mod 20
d x 7 mod 20 = 1
d x 7 = 21
d = 23
b) In a Diffie-Hellman key exchange, suppose that Alicia and Brad agree to use the modulus q = 47 and generator a = 5. Alicia (A) chooses the secret value x = 18 and Brad (B) chooses his secret value y = 22. Answer the following questions and show the relevant steps to obtain your answer.
Ans:
modulus q = 47 and generator a = 5.
Secret value, XA = 18
Secret value, YB = 22
i) What is the public value h1 computed by Alicia which is sent to Brad?
Ans:
h1 = aXA mod q
h1 = 518 mod 47
h1 = 2
ii) What is the public value h2 computed by Brad which is sent to Alicia?
Ans:
h2 = aYB mod q h2= 522 mod 47 h2 = 28
iii) What is the secret key kA computed by Alicia and the secret key kB computed by Brad?
Ans:
KA = h2XA mod q
KA = 2818 mod 47
KA = 24
KB = h1YB mod q KB = 222 mod 47 KB = 24
c) Alice wants to set up a business company that securely deals with her clients. Bob is a potential client that Alice wants to have a good connection. As a security consultant, your job is to devise a plan to establish a secure information exchange. The assumption is made that Alice and Bob already have their public and public keys; (PrivA, PubA) and (PrivB, PubB) respectively, and both of them have exchanged their public key beforehand. Your plan includes comprehensive protocols to secure all messages, according to Alice’s requirements below. Discuss your answers.
i) Integrity: Alice and Bob want to make sure that every message sent cannot be forged by anyone.
Ans:
I will suggest Alice to use message authentication code (MAC). For this case, Alice can send the message along with the MAC, the Bob who receive the message can feed the message and the private key into the MAC algorithm to re calculate the MAC value. The calculate MAC can be used to check with the received MAC which is sent by Alice. If the MAC value is not match to each other, then Bob can detect this message is forged by other.
ii) Authenticity: Alice and Bob can verify that messages actually came from them.
Ans:
I will suggest Alice to use Digital Signature (DS).The message can be encrypted with hash using Alice’s private key to generate a signature. This signature can be attached with message before sending to Bob. After Bob receives the message, the message can be decrypted using Alice’s public key. If the calculated hash is not match with original hash then Bob can suspect this message might be sent by others.
iii) Confidentiality: Alice exchanges business-related documents with Bob in a way, so that Alice and Bob may open, read or modify the documents.
Ans:
I will suggest Alice to use RSA algorithm (encryption method). The value of p and q has been set and agreed by Alice and Bob. Then Alice can generate ciphertext message by encrypting the plaintext using both RSA algorithm and Bob’s public key. Then Alice sends ciphertext message to Bob. Bob can decrypt the ciphertext message back into plaintext by using the his private key.
27a. List some security threats related to mobile devices.
Ans:
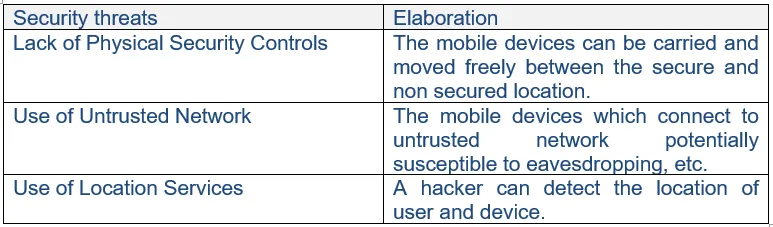
27b. What security areas are addressed by IEEE 802.11i?
Ans:
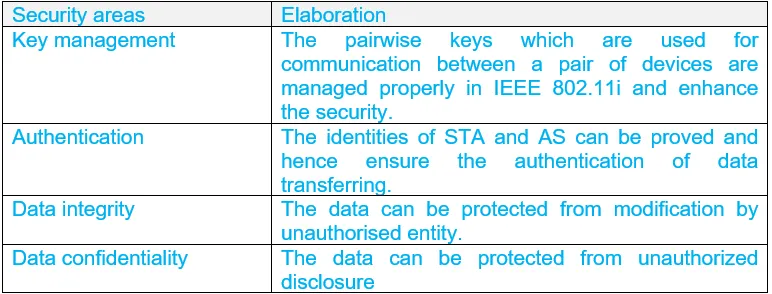
27c. Classify viruses based on the targets they try to infect.
Ans:
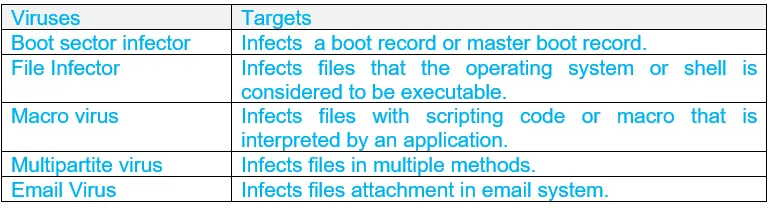
28a. List and briefly define three classes of intruders
Ans:

28b. List the direct approaches that can be implemented to counter insider attacks.
Ans:
i. To monitor the access record and the entering commands of users by setting the logs.
ii. Strong authentication is used to protect the sensitive resources.
iii. The employee’s network access and computer account shall be deleted upon their termination.
iv. To apply limitation on the employee’s privilege.
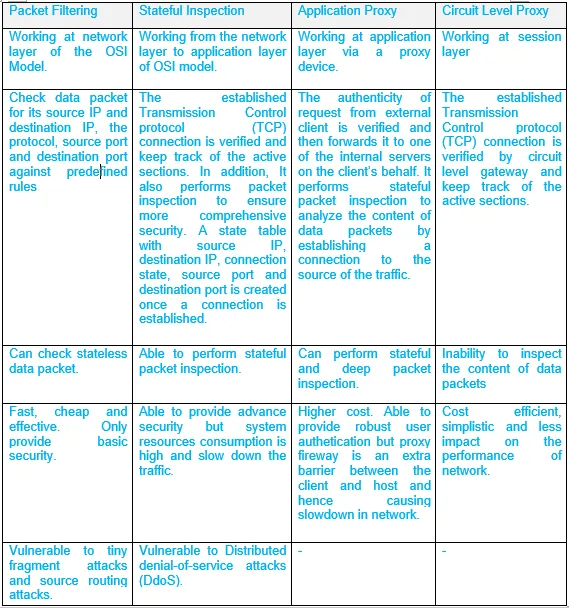
28c. What are the differences among the type of firewalls shown in Figure below?
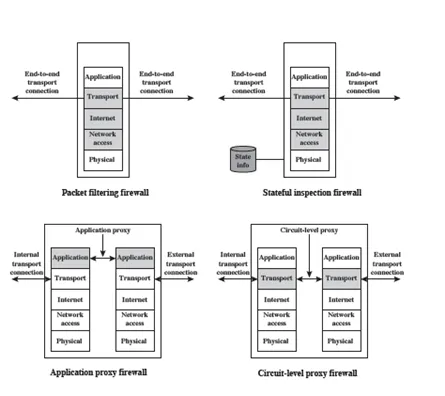
Ans:
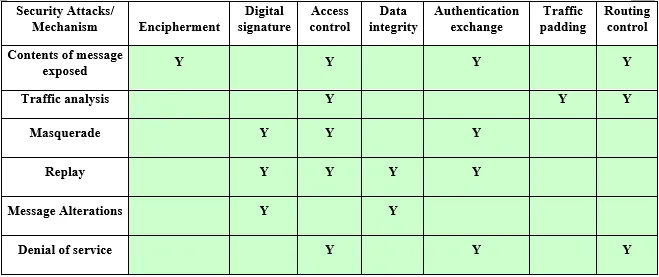
29. Figure below shows the relationship matrix between the security mechanism specified in X.800 and security services. Provide a similar matrix that indicates the association between this list of attacks (denial of service, contents of message exposed, traffic analysis, masquerade, replay and message alterations) and security mechanism.
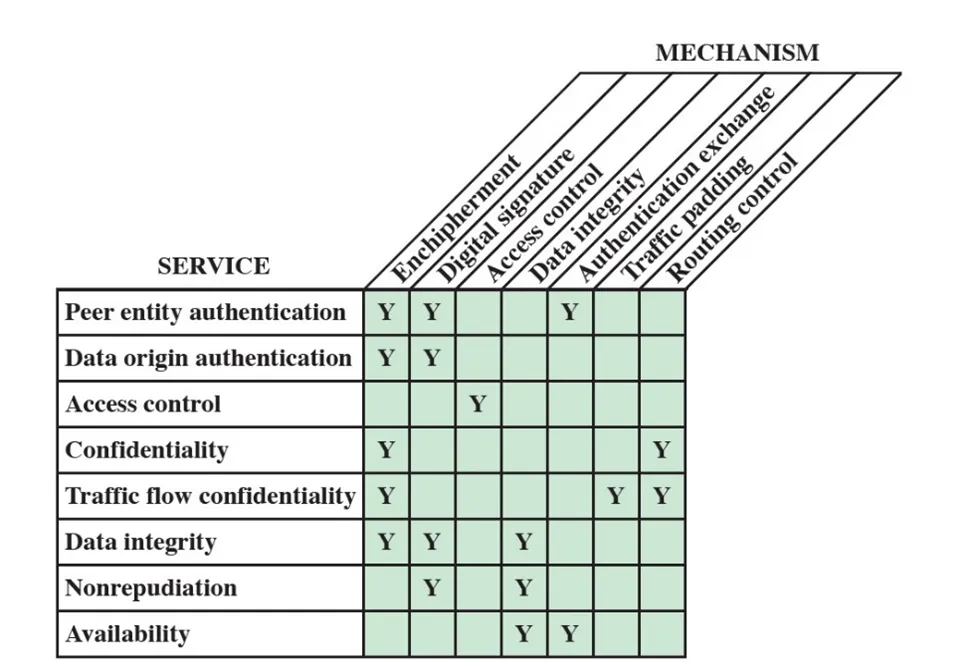
Ans:
30. Symmetric Encryption and Message Confidentiality
a) Figure below shows the Cipher Block Chaining (CBC). There is an error in the transmitted Ciphertext no 1.
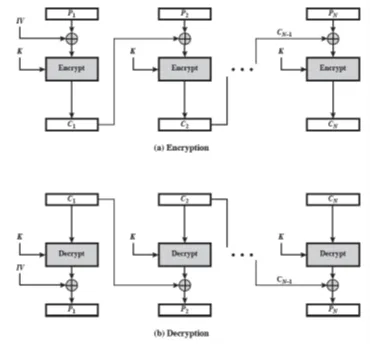
i) Is there any block further than P1 is affected?
Ans:
Only P1 and P2. For example, suppose C1 is corrupted. The output block P3 depends only on the input blocks C2 and C3.
ii) Suppose there is a bit error in the source version of P1. Through how many ciphertext blocks is this error propagated? What is the effect on the receiver?
Ans:
An error in P1 affects C1. But since C1 is input to the calculation of C2, C2 is affected. This effect carries through indefinitely so that all ciphertext blocks are affected. However, at the receiving end, the decryption algorithm restores the correct plaintext for blocks except the one in error. Therefore, the error only affects the corresponding decrypted plaintext block (P1)
iii) Identify which decrypted plaintext blocks Px will be corrupted if there is an error in block C4 of the transmitted ciphertext.
Ans:
Ciphertext block Ci is used as input to the XOR function when obtaining plaintext blocks Pi and Pi+1. Therefore, a transmission error in block C4 will corrupt blocks P4 and P5 of the decrypted plaintext but will not propagate to any of the other blocks.
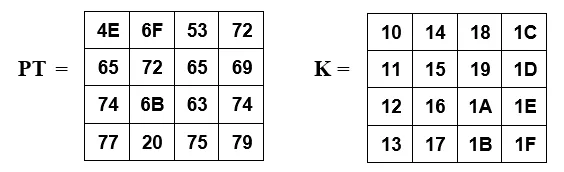
31a. Given the plaintext in ASCII characters [Network Security] and the key is the XOR product between a hexadecimal string of (10101010101010101010101010101010)hex and [000102030405060708090A0B0C0D0E0F]hex.
i) Show the content in the state form for both plaintext and the key.
Ans:
31b. Write down the w0, w1, w2 and w3.
Ans:
wo = 10111213, w1 = 14151617, w2 = 18191A1B, w3 = 1C1D1E1F
31c. The output of SubBytes operation is given as follows:
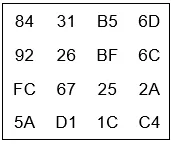
Ans:
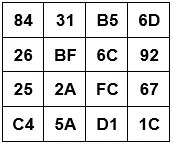
Perform the ShiftRows operation and write down the output.
31c. AES and DES are the two widely used block-ciphers in symmetric cryptography. For every following component of DES, state the comparable element in AES, or describe why it is not required/used in AES.
i) XOR of the f function output with the left half of the block
Ans:
The MixColumn step because this is where the different bytes interact with each other.
ii) The f function
Ans:
The ByteSub step, because it contributes nonlinearity to AES.
iii) Permutation P
Ans:
The ShiftRow step, because it permutes the bytes.
iv) Swapping of halves of the block
Ans:
There is no wholesale swapping of rows or columns. AES does not require this step because: The MixColumn step causes every byte in a column to alter every other byte in the column, so there is not need to swap rows; The ShiftRow step moves bytes from one column to another, so there is no need to swap columns
32. Asymmetric Encryption and Message Authentication
a) The primitive root of a prime number is the basic principle of Diffie-Hellman.
i) Is 3 the primitive root of 11? Show the proof with your calculation.
Ans:
No (with proof)
ii) What are the important criteria for selecting a prime number in cryptography? Is 11 a good choice for such a purpose?
Ans:
Mathematically difficult to compute (such as difficult to find a prime factorization) to prevent a brute force attack. Usually a large prime number is selected. Hence, 11 is really a bad choice for prime number in cryptography since it is easy to compute. b) Find the parameters stated using the Diffie-Hellman methods, given the user A and B shared a prime number and its primitive root of 23 and 5, respectively.
i) If user A public key value is 8, find the A’s private key.
Ans:
q = 23, α = 5, YA = 8
YA = α^XA mod q
8 = 5 ^ XA mod 23
5 ^ 1 mod 23 = 5
5 ^ 2 mod 23 = 2
5 ^ 3 mod 23 = 10
5 ^ 4 mod 23 = 4
5 ^ 5 mod 23 = 20
5 ^ 6 mod 23 = 8
Therefore XA = 6
ii) If user B public key value is 19, what is the common secret key?
Ans:
KAB = αXA.XB mod q
= YAXB mod q (which B can compute)
= YBXA mod q (which A can compute)
= 196 mod 23 = 47045881 mod 23 = 2
Therefore K(Shared Secret Key) = 2
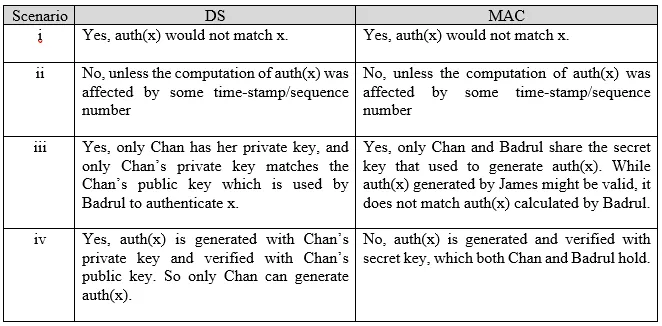
33. In the following scenario, we will compare the security services that are given by digital signatures (DS) and message authentication codes (MAC). We assume that James can read all messages send from Chan to Badrul and the other way around, too. James has no knowledge of any keys but the public one in the case of DS. State whether and how (i) DS and (ii) MAC protect against each attack. The value auth(x) is calculated with DS and MAC’s algorithm, correspondingly.
i) (Message integrity) Chan sends a message x = “Transfer RM200 to Darren” in the clear and also sends auth(x) to Badrul. James intercepts the message and replaces “Darren” with “James”. Will Badrul detect this?.
ii) (Replay) Chan sends a message x = “Transfer RM200 to James” in the clear and also sends auth(x) to Badrul. James observes the message and signature and sends them 100 times to Badrul. Will Badrul detect this?
iii) (Sender Authentication with the cheating third party) James claims that he sent some message x with a valid auth(x) to Badrul, but Chan claims the same. Can Badrul clear the question in either case?
iv) (Authentication with Badrul cheating) Badrul claims that he received a message x with a valid signature auth(x) from Chan (e.g., “Transfer RM200 from Chan to Badrul”) but Chan claims she has never sent it. Can Chan clear this question in either case?
Ans:
34. You are given the following parameters in RSA cryptosystem:
p = 11, q = 13, e = 13
a) Find the integer d.
Ans:
n = pq = 143, (n) = (p – 1)(q – 1) = 120
Find d and e so that de mod 120 = 1, find this number so that gcd of this number is d*e.
e = 13, de mod 120 = 1, so d = 37.
34b. List down the public key and private key.
Ans:
PU = {13, 143}, PR = {37, 143}
You need to encrypt the plaintext message, M = OF.
34c. Convert this message to value according to ASCII table.
To encrypt this message, you can either combine the value, or separate it into the blocks of 2 digits (Hint: it must satisfy the condition M < n). Ans:
M1 = O = 79, M2 = F = 70
M = 7970
34d. Encrypt and decrypt the message OF.
To encrypt this message, you can either combine the value, or separate it into the blocks of 2 digits (Hint: it must satisfy the condition M < n).
M must less than n, M < n, n = 143
M1 = 79, 79 < 143
C1 = M1^e mod 143
79^13 mod 143
[79^12 mod 143 * 79^1 mod 143] mod 143
[79^2 mod 143 * 79^2 mod 143 * 79^2 mod 143 * 79^2 mod 143 * 79^2 mod 143 * 79^2 mod 143 * 143 * 79 mod 143] mod 143
79^2 mod 143 = 92, 92^6 mod 143 = 92
79 mod 143 = 79
C1 = 92*79 mod 143 = 118
M2 = F = 70
70 < 143
C2 = M2^13 mod 143
70^13 mod 143
[70^12 mod 143 * 70 mod 143] mod 143
[70^8 mod 143 * 70^4 mod 143 * 70 mod 143] mod 143
[53*14*70] mod 143
C2 = 31
To decrypt:
M1 = C1^d mod 143
= 118^37 mod 143 <<< similar step as above (breakdown into smaller set)
= 79
M1 = 79 which is ASCII for ‘O’
M2 = C2^37 mod 143
= 31^37 mod 143 <<< similar step as above (breakdown into smaller set)
= 70
M2 = 79, which ASCII for ‘F’
34e. If the decimal value (not character) of ciphertext is 188267, decrypt this value and convert it to an appropriate message according to the ASCII table.
Ans:
C1=18, C2=82 and C3=67
M1 = C1^d mod 143
= 18^37 mod 143
= 83
M2 = C2^d mod 143
= 82^37 mod 143
= 69
M3 = C3^d mod 143
= 67^37 mod 143
= 67
M = 836967 = SEC
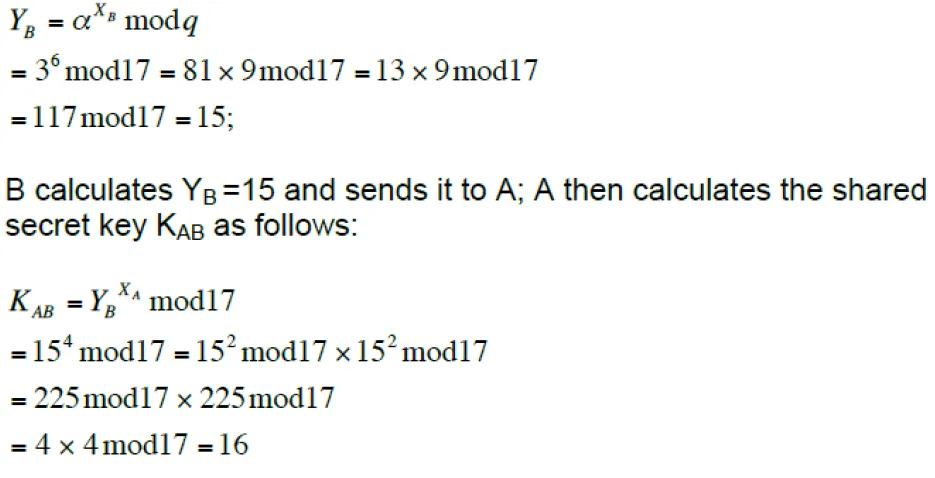
35. Consider a Diffie-Hellman scheme with a common prime q = 17 and a primitive root α = 3.
a) If user A has a private key XA=4, what is A’s public key, YA?
Ans:
YA = aXA modq = 3XA mod17; 34 mod17 = 81mod17 =13;
35b. A sends YA to B. If B has a private key XB=6, what is the shared secret key, K that B can calculate and share with A?
Ans:

35c. If B computes YB and sends it to A, what is the shared secret Key, K computed by A?
36. In the steps of “Append the padding bits” in SHA-512 system (shown in Figure below), the message is padded so that its length is congruent to 896 mod 1024 or (length ≅ 896 mod 1024). State the value of the following padding field is the message length is:
a) 1919
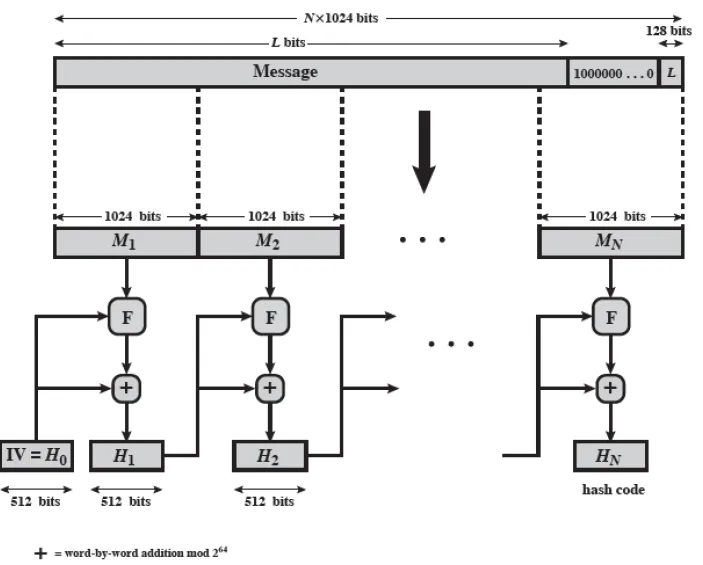
Ans:
1919 mod 1024 = 895
So, to make it 896, we need to deduct the value:
896 – 895 = 1 bit #
b) 1920
Ans:
1920 mod 1024 = 896, so this is desired value, meaning that we need to add the whole value of 1024 for this padding field.
So we add 1024 bits more to make congruent to 896 mod 1024.
c) 2942
Ans:
2942 mod 1024 = 894
So, to make it 896, we need to deduct the value:
896 – 894 = 2 bits #
37. What is the correct value of SHA-512 message-length filed if the message length is:
a) 3967
Ans:
still 3967 (message length field does not affect anything, only you have to add at padding field)
b) 3968
Ans:
still 3968
38. What problem was Kerberos designed to address?
Ans:
The problem that Kerberos addresses is this: Assume an open distributed environment in which users at workstations wish to access services on servers distributed throughout the network. We would like for servers to be able to restrict access to authorized users and to be able to authenticate requests for service. In this environment, a workstation cannot be trusted to identify its users correctly to network services.
39. What four requirements were defined for Kerberos?
Ans:
Secure: A network eavesdropper should not be able to obtain the necessary information to impersonate a user. More generally, Kerberos should be strong enough that a potential opponent does not find it to be the weak link.
Reliable: For all services that rely on Kerberos for access control, lack of availability of the Kerberos service means lack of availability of the supported services. Hence, Kerberos should be highly reliable and should employ a distributed server architecture, with one system able to back up another.
Transparent: Ideally, the user should not be aware that authentication is taking place, beyond the requirement to enter a password.
Scalable: The system should be capable of supporting large numbers of clients and servers. This suggests a modular, distributed architecture
40. What are the essential ingredients of a public-key directory?
Ans:
a. The authority maintains a directory with a {name, public key} entry for each participant.
b. Each participant registers a public key with the directory authority. Registration would have to be in person or by some form of secure authenticated communication.
c. A participant may replace the existing key with a new one at any time, either because of the desire to replace a public key that has already been used for a large amount of data, or because the corresponding private key has been compromised in some way.
d. Periodically, the authority publishes the entire directory or updates to the directory. For example, a hard-copy version much like a telephone book could be published, or updates could be listed in a widely circulated newspaper. Participants could also access the directory electronically. For this purpose, secure, authenticated communication from the authority to the participant is mandatory.
More Free Exercises:
Data Science ExercisesBig Data Management Exercises
Principle in Data Science Exercises
Data Analytics Exercises
Data Mining Exercises
Network Security Exercises
Other Exercises:
Python String Exercises
Python List Exercises
Python Library Exercises
Python Sets Exercises
Python Array Exercises
Python Condition Statement Exercises
Python Lambda Exercises
Python Function Exercises
Python File Input Output Exercises
Python Tkinter Exercises